Data centers don’t fail in just one way—and they’re rarely breached through just one weakness. In 2026, the most resilient operators treat security as a stack of mutually reinforcing controls across physical protection, identity, networks, data handling, and daily operations.
That “defense-in-depth” approach matters even more now that threats blend disciplines: a phishing attempt becomes a badge-clone attempt; a contractor ticket becomes a privilege escalation; a BMS remote session becomes an entry point into critical networks.
What follows are ten practical security layers that wrap around mission-critical data center assets. Each layer is valuable on its own—but the real strength comes from how they connect.
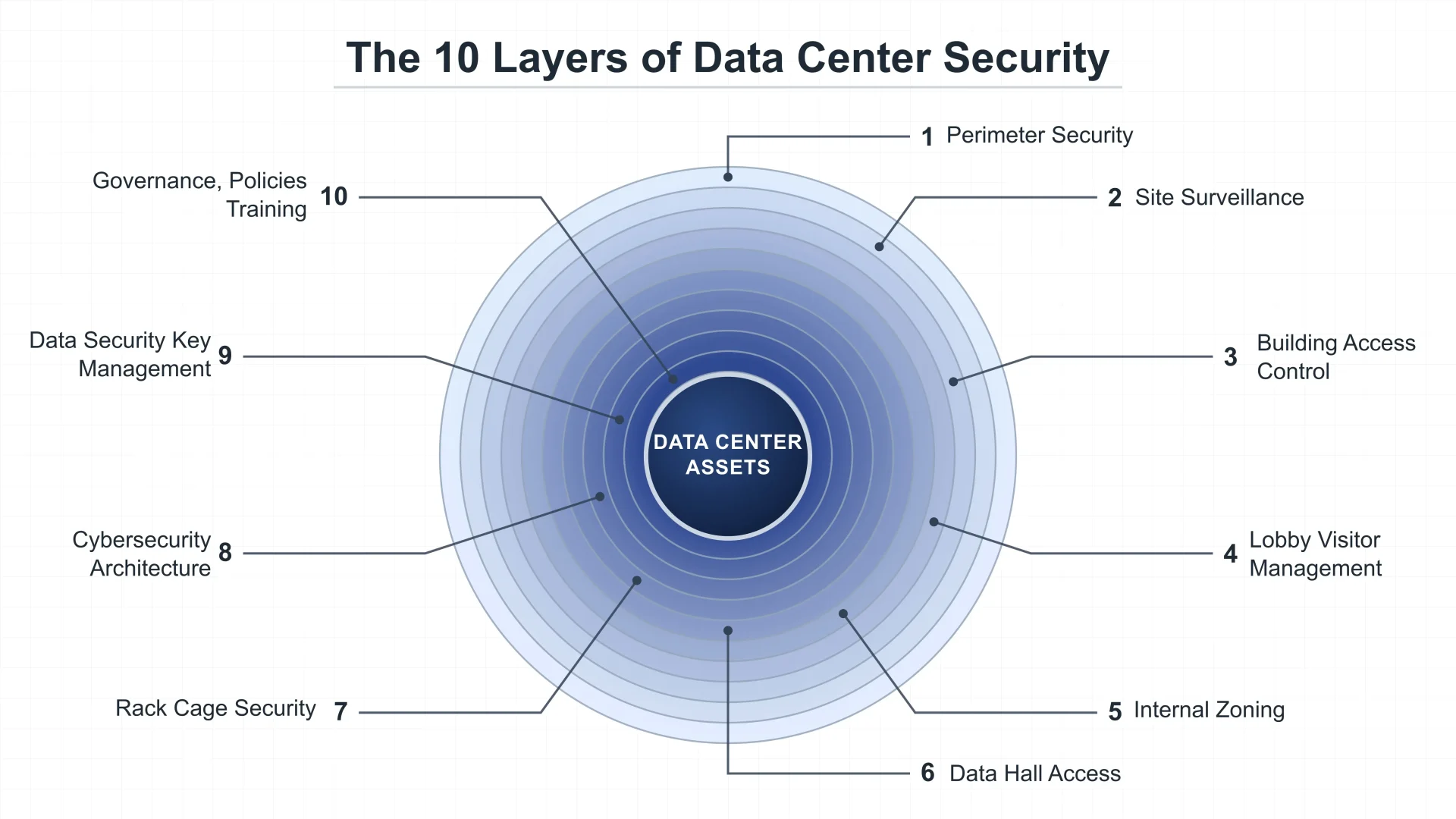
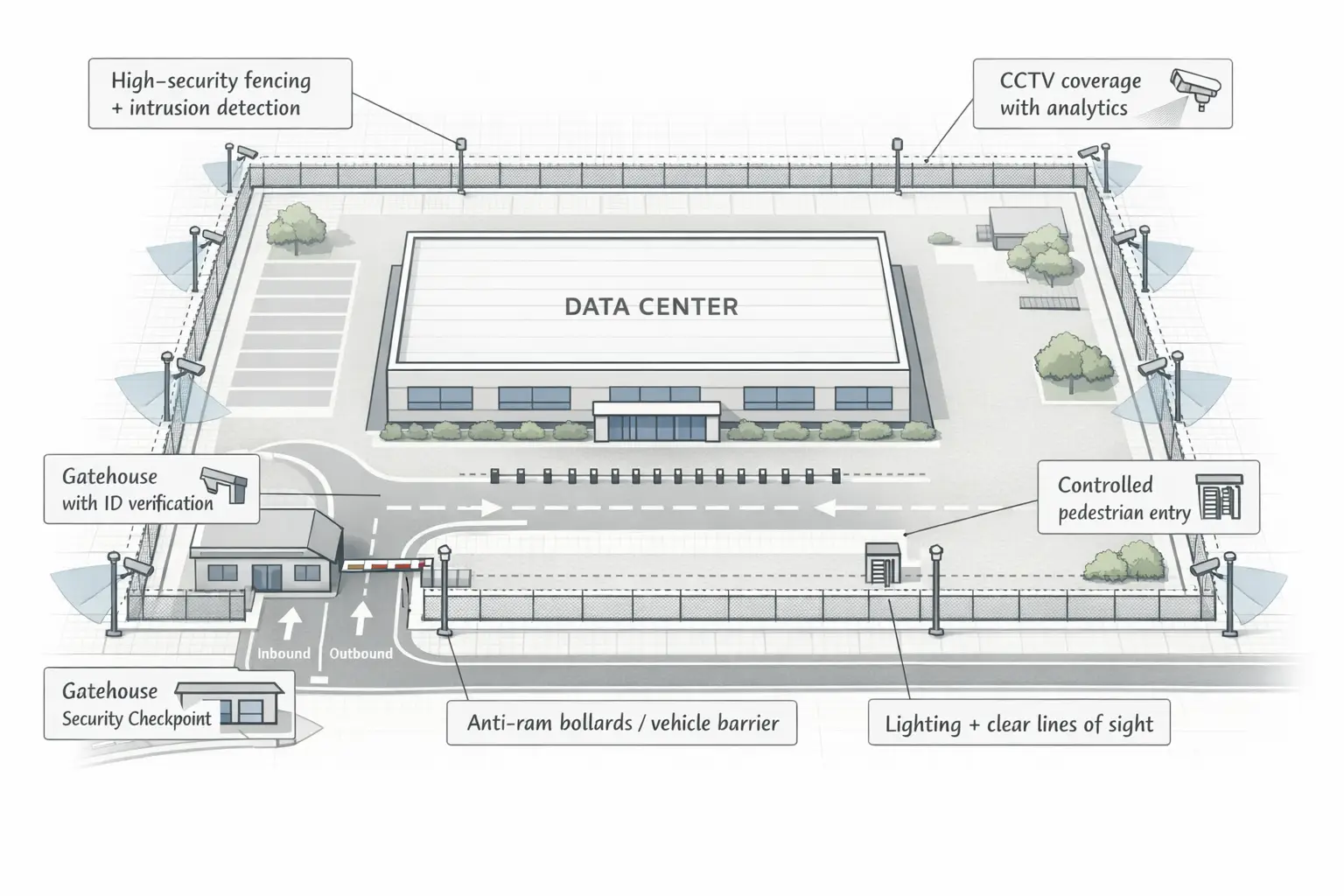
1) Perimeter security (keep threats outside the line)
Perimeter controls are about deterrence, delay, and detection. The goal is to prevent unauthorized approach and create time for response—especially important for sites with large footprints, multiple gates, or nearby public access.
Best-practice controls
- Rated fencing + anti-ram protection (bollards / barriers) at vehicle approaches
- Perimeter intrusion detection (fence vibration sensors, buried cable, radar/LiDAR where justified)
- Lighting + camera coverage designed as a system (avoid “dark pockets,” manage glare)
- Standards alignment: TIA-942 includes security requirements within DC infrastructure scope; EN 50600 also addresses DC physical security in a structured way
2) Site surveillance (see, correlate, respond)
Surveillance in 2026 is less about “more cameras” and more about correlation and workflow: turning video, alarms, and access events into a reliable decision cycle. AI analytics can help, but only when tuned and governed (false positives and “alert fatigue” are real operational risks).
Modern practices
- Analytics with rules you can defend (line-crossing, loitering, object removal, after-hours movement)
- Event correlation between camera + door + fence + motion for faster verification
- Clear escalation paths (SOC/GSOC dispatch, incident severity levels, call-out trees)
Useful framework tie-ins
- ISO 27001 supports a governance model for consistent controls and continuous improvement
3) Building access control (the front door is an identity system)
At the entrance, the mission is simple: only authorized people enter—and only under the right conditions. What’s changed is the mindset: identity isn’t static. Access should reflect risk, role, and context.
Modern practices
- Multi-factor physical entry (badge + biometric or badge + mobile credential)
- Mantraps / interlocks for high-sensitivity areas
- Role- and time-bound permissions (shift-based, project-based, auto-expiry)
- Zero Trust thinking: treat every access attempt as a verification event, not a default trust

4) Lobby & visitor management (your highest-variance risk)
Visitors, vendors, and short-term contractors are where process breaks first—because they introduce variability. Strong sites reduce this risk by making visitor handling structured, logged, and constrained.
Modern practices
- Pre-registration + ID verification and explicit sponsor approval
- Visitor badges that expire automatically
- Escorted access rules for sensitive zones
- Defined “guest-only” pathways (no wandering—design the flow)
5) Internal zoning (restrict movement inside the building)
Once inside, the security job becomes “need-to-access.” The more you can segment the facility into zones, the more you can limit both accidental exposure and deliberate insider movement.
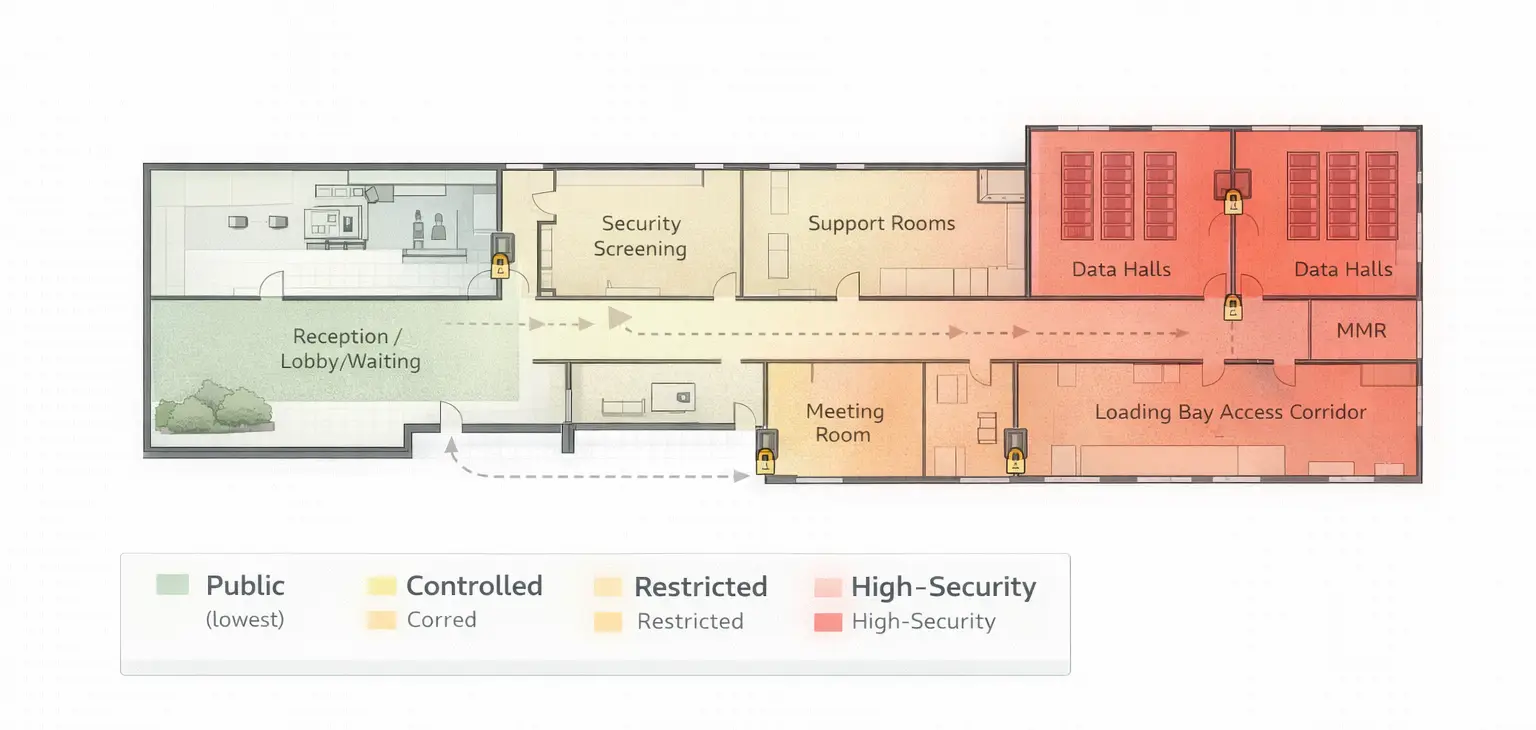
Modern practices
- Zone-based permissions (floor, suite, pod, MMR, security room, loading)
- Elevator / turnstile integration (credentials required for restricted floors)
- Anti-tailgating controls at critical interior boundaries
6) Data hall / server room thresholds (protect the core)
The white space is where attackers can shift from nuisance to catastrophe. High-security operators treat the data hall threshold as a high-assurance checkpoint—and link it to operational procedures.
Modern practices
- Two-person rule for highly sensitive environments (where justified by risk)
- Biometrics with liveness detection (reduce spoofing attempts)
- Strict tool/media control (what comes in, what leaves, how it’s logged)
7) Rack & cage security (physical tamper resistance + accountability)
Rack-level security is especially important in colocation and multi-tenant environments, where proximity increases risk. The aim is to ensure every cabinet interaction is attributable and reviewable.

Modern practices
- Electronic rack locks with audit trails (who/when/which door)
- Cages and partitioning that match tenant boundaries
- Asset tagging and chain-of-custody for drives, NICs, removable media
8) Cybersecurity architecture (assume breach, prevent lateral movement)
In 2026, the most common “big incident” pattern is still: initial access → privilege escalation → lateral movement → impact. Data centers reduce blast radius by designing networks so compromise doesn’t spread easily.
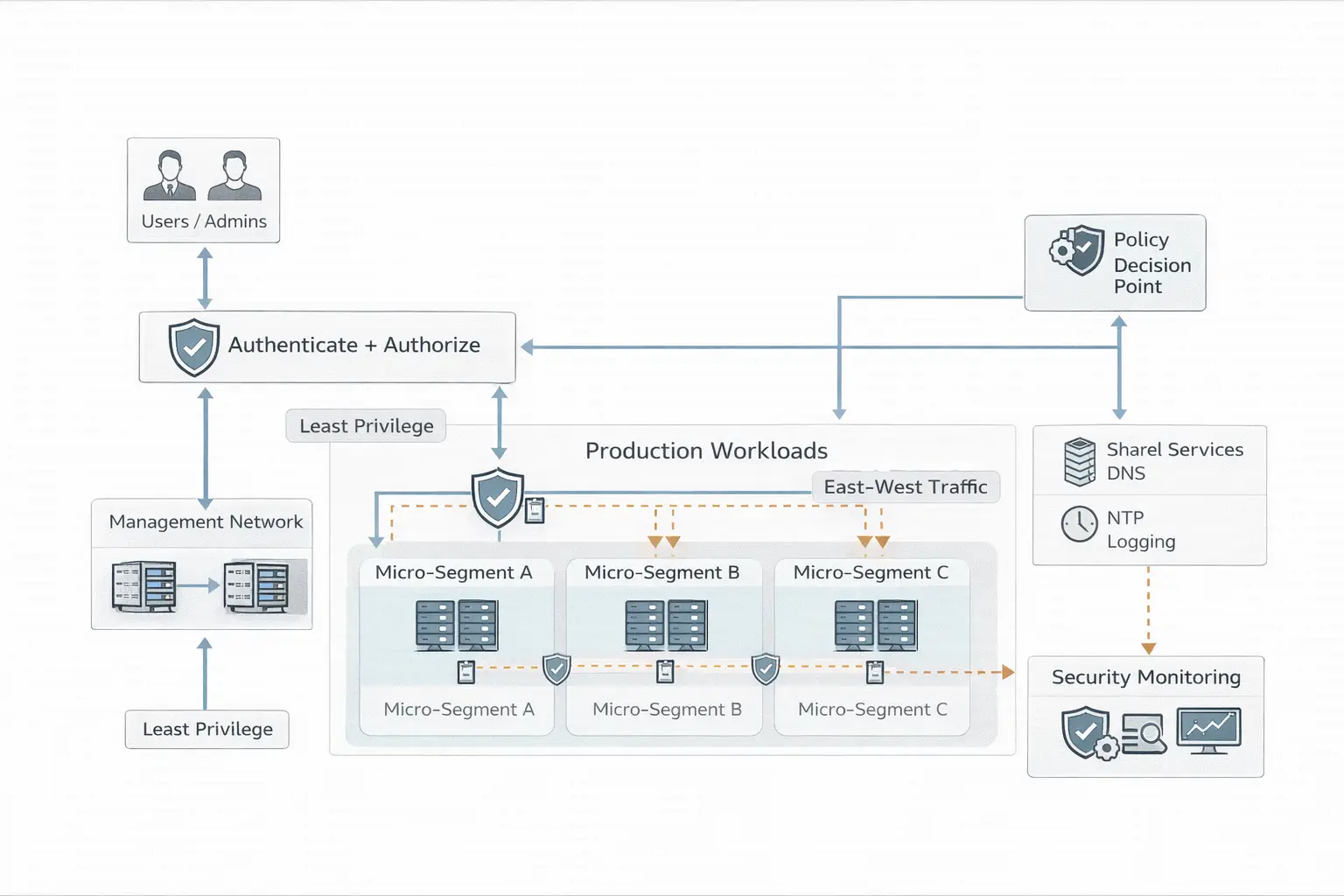
Modern practices
- Micro-segmentation (limit east-west movement)
- Zero Trust Architecture principles (policy enforcement close to the resource)
- Continuous monitoring and control catalogs aligned to recognized baselines such as NIST SP 800-53 Rev. 5
- Controls mapping to CIS Controls v8 for prioritization and maturity planning
9) Data security (keys, encryption, retention, and recovery)
Physical security and cyber security meet at the data layer. If attackers can reach systems physically—or impersonate authorized operators—then key management, encryption, and backup integrity determine whether you have a breach or a business-ending event.

Modern practices
- Encryption at rest and in transit with enforceable policy
- HSM-backed key protection for high-value environments
- Immutable / tamper-resistant backups and tested recovery paths
- Compliance reality check: PCI DSS v4.0 is the active standard, and by 2026 its requirements are fully in force for the payment environment
10) Operational governance, policies & training (the layer that makes the rest real)
Technology doesn’t run itself. Security posture is largely determined by how people behave under stress: after-hours callouts, urgent customer requests, failed change windows, and “just this once” exceptions.
This is where 2026 guidance is especially clear: security must be governable, measurable, and owned. NIST CSF 2.0’s addition of “Govern” fits perfectly here—security isn’t only a technical function; it’s an enterprise risk function.
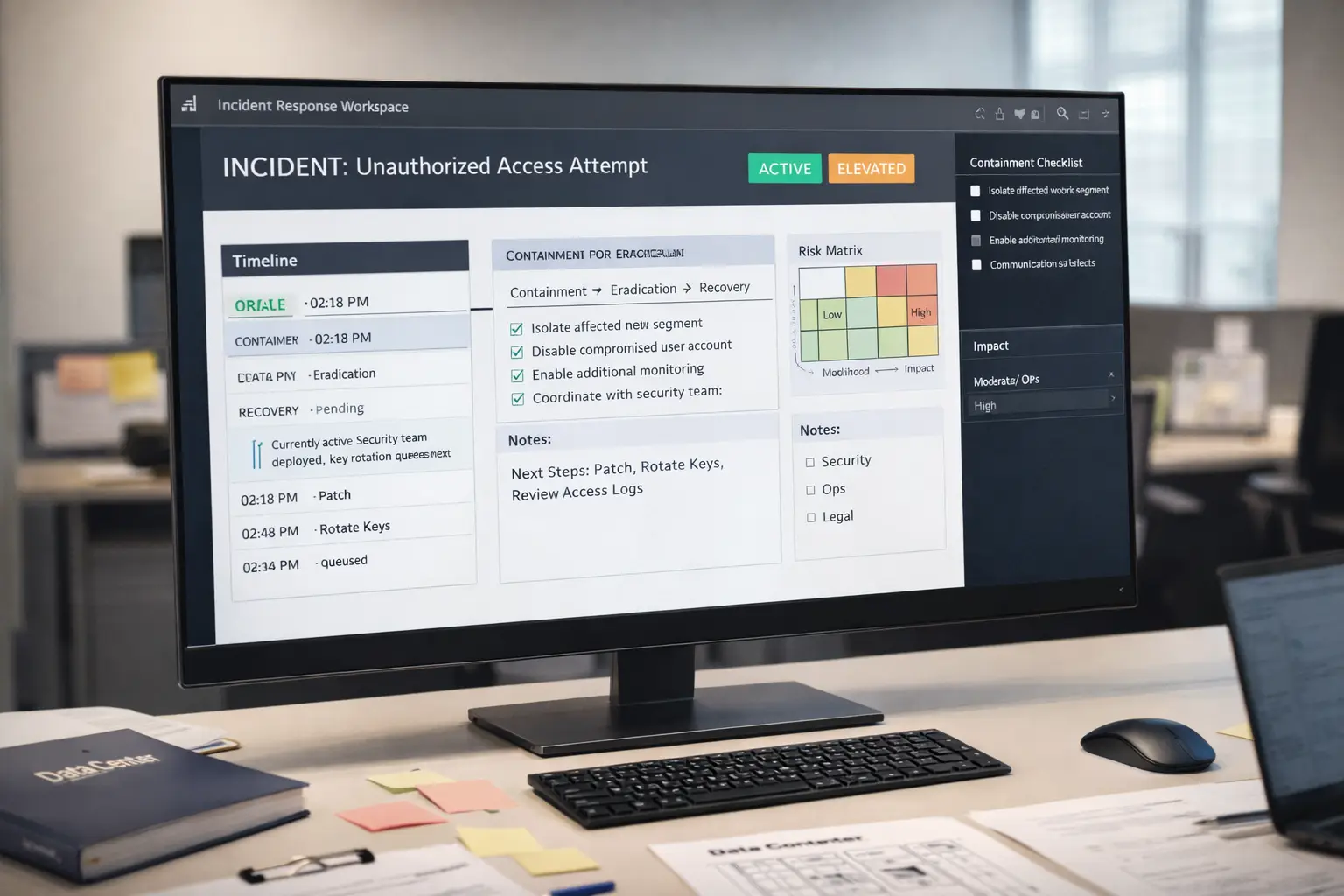
Modern practices
- Tabletop exercises (intrusion, ransomware, insider, supply chain compromise)
- Red-team / blue-team testing across physical + cyber scenarios
- Vendor governance (remote access rules, logging, expiry, periodic re-approval)
- BC/DR alignment via business continuity frameworks like ISO 22301
Conclusion: security is a system, not a checklist
A “ten-layer” model isn’t about adding complexity—it’s about building controlled overlap so no single failure becomes a catastrophic event. In 2026, the strongest data center security programs connect:
- Facility zoning + identity assurance
- Physical events + SOC correlation
- Access rights + cyber segmentation
- Key protection + recovery discipline
Use ISO 27001 as the governance backbone, apply Zero Trust concepts to both identity and network design, align physical security with DC standards like TIA-942 and EN 50600 where applicable, and keep Tier ratings in their proper lane (availability topology—not security).
How Azura Consultancy Can Help You Operationalize “Defense-in-Depth”
Designing ten layers of security is easy on paper. Making them work together—day after day, across people, process, and technology—is where most data centers feel the friction: inconsistent access rules, gaps between physical security and cyber monitoring, unclear ownership, and controls that don’t translate into auditable evidence.
Azura Consultancy helps organizations turn security intent into engineered, verifiable outcomes—by aligning security architecture with the realities of mission-critical operations (availability, maintainability, compliance, and contractor-heavy workflows). Our work spans data center engineering design, technical due diligence, and implementation support, so the security model is not just “recommended,” but buildable, operable, and testable.
Turn Data Center Security Into Operational Proof
Azura Consultancy helps owners, operators, and investors engineer defense-in-depth that actually works—integrating physical security, identity, monitoring, and governance into a security posture you can audit, operate, and trust. Contact Us Today!
Where Azura delivers the most value for data center security
1) Security-by-design (physical + MEP + operational integration)
We embed physical security, access control, and monitoring requirements into the broader facility design—so perimeter, mantraps, zoning, and critical-room thresholds are engineered to match resiliency, maintenance, and operational constraints (not bolted on later).
2) Converged governance: connecting facility access to cyber controls
Modern security depends on how well your identity model, access permissions, and monitoring workflows connect across domains. We help define the “handshake” between physical access events and logical access posture, improving traceability and reducing blind spots in investigations and audits.
3) Independent Technical Due Diligence that validates what’s real
For owners, lenders, and investors, we perform technical due diligence that includes reviewing and assessing physical and environmental security measures (access control, surveillance, fire protection, and related risk controls) alongside core infrastructure performance and compliance readiness.
What you can engage Azura to do (practical deliverables)
- Security and access-control system design aligned to facility zoning and operational workflows
- Site and facility risk reviews (what’s missing, what’s redundant, what’s unverifiable)
- Operational readiness + evidence packs: policies, procedures, logging expectations, audit trails, and test scenarios that prove controls work under stress
- Engineering coordination across MEP, fire/life safety, monitoring, and resilience requirements (so security doesn’t compromise maintainability)
- Specialist analysis where needed (e.g., data hall airflow/containment impacts, certification support, and mission-critical engineering services)
The outcome
You get a security posture that is:
- Layered (no single point of failure)
- Auditable (clear logs, ownership, and evidence)
- Operationally realistic (works with contractors, changes, and maintenance windows)
- Aligned to uptime expectations (security that supports reliability, not conflicts with it)