What Investors Now Demand For Data Centers + Energy Assets
In 2026, technical due diligence (TDD) for mission-critical assets has shifted from “Is it built to spec?” to “Can it survive real-world stress and still deliver the investment thesis?” That’s a bigger question—and it forces a different kind of diligence.
Investors, lenders, and acquisition teams are now looking for proof: operational evidence, testing records, constraint analysis, and a clear translation from engineering reality to capex timing, opex exposure, and valuation risk. Labels and marketing tiers don’t disappear, but they don’t close the gap between a glossy design claim and what actually happens at 2:00 a.m. during a grid event, equipment failure, or a rushed expansion.

Why technical due diligence changed in 2026
Mission-critical assets used to be evaluated primarily on design intent: redundancy diagrams, equipment schedules, and “N+1” claims. Those still matter, but they’re no longer enough. What changed is the scale of consequence.
Data centers have become power-first infrastructure, and energy assets are increasingly judged by reliability, integration readiness, and constraint exposure. The diligence conversation now starts earlier and goes deeper because the downside isn’t theoretical: delays, curtailment, unplanned downtime, compliance exposure, and stranded expansion plans all show up as real financial outcomes.
A modern TDD has to answer three uncomfortable questions:
- Can it operate reliably under realistic failure scenarios?
- Can it scale without hitting a wall—power, water, permitting, space, or delivery complexity?
- Can it be integrated and operated safely after acquisition without creating new blind spots?
When investors push harder on diligence, it’s not because they want a thicker report. It’s because they want fewer surprises.
What technical due diligence is (and what it is not)
Technical due diligence is not a design review. It’s not a marketing validation exercise. And it’s not a checkbox condition survey.
Investor-grade TDD is a decision tool. It connects the asset’s technical reality to deal outcomes: purchase price, warranties, covenants, capex schedules, operational risk reserves, and post-close integration plans.
At a practical level, that means the diligence process must do four things well:
- Verify (not just accept) technical claims with evidence
- Quantify operational risk in a way investors can underwrite
- Translate findings into capex/opex timing and business impact
- Prioritise fixes into “must-do” vs “value creation” vs “optional”
If your TDD doesn’t change decisions, it’s not doing its job.
The investor-grade TDD workflow (repeatable and board-ready)
A strong diligence process is structured enough to be repeatable across portfolios, but flexible enough to reflect the deal thesis. In 2026, the best TDD workflows follow a familiar rhythm:
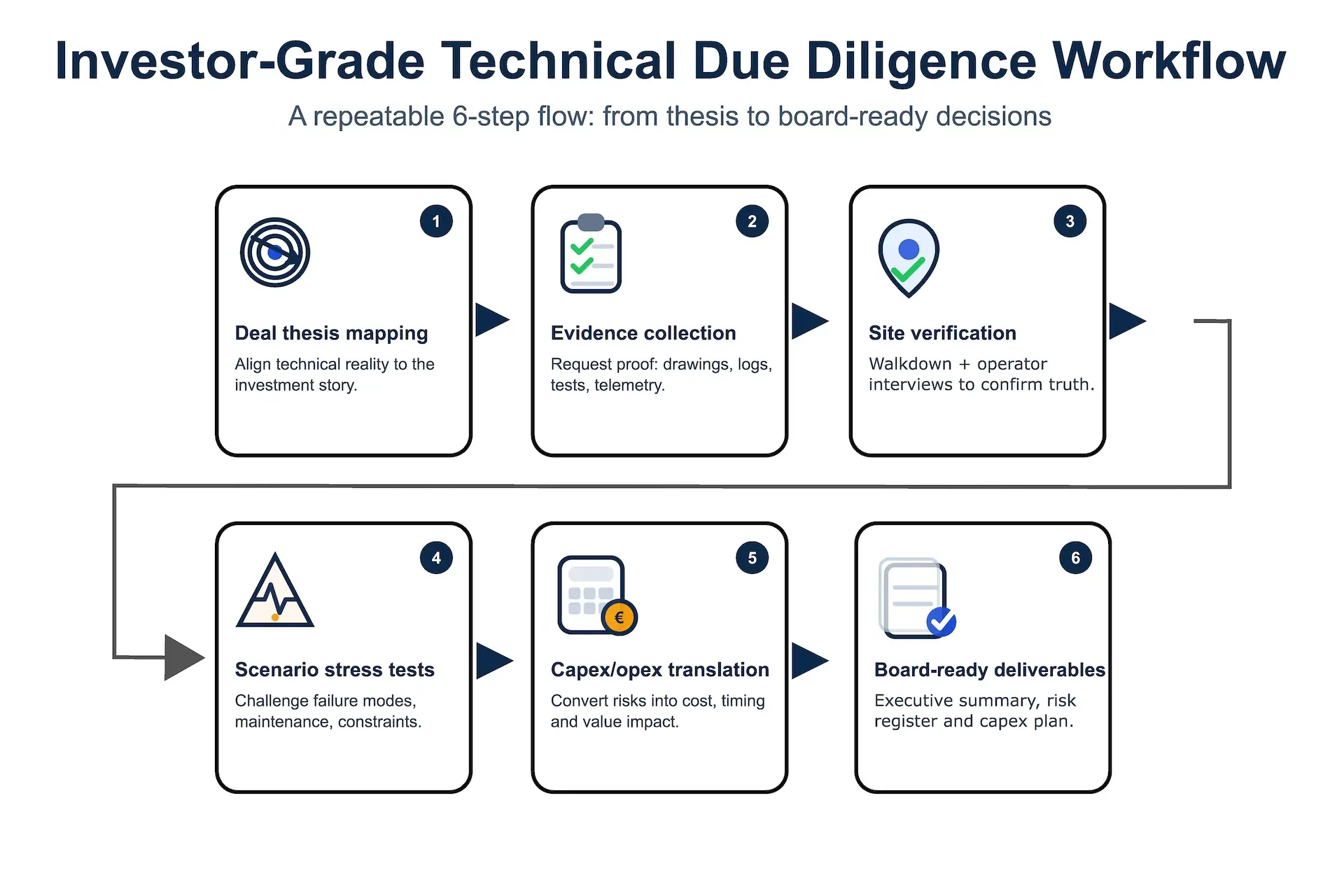
A strong diligence process is structured enough to be repeatable across portfolios, but flexible enough to reflect the deal thesis. In 2026, the best TDD workflows follow a familiar rhythm:
1) Map the deal thesis to technical reality
Start with the investment story: growth, resilience, location advantage, power access, sustainability claims, customer profile, and margin expectations. Then ask: what technical conditions must be true for this story to hold?
2) Evidence collection (before the site visit)
The fastest way to raise diligence quality is to get serious about documentation and data. Drawings and single-lines matter, but so do operating procedures, testing records, alarms history, maintenance backlogs, and change control.
3) Site verification (walkdown + interviews)
Site walks confirm what documents can’t: maintainability, access, operational behaviour, and the culture of “how work gets done.” Interviewing operations staff often reveals more risk than any spec sheet.
4) Stress-test the asset under credible scenarios
Don’t just check redundancy—challenge it. What happens during maintenance? What happens when the “redundant” unit is locked out? What happens when utility conditions shift?
5) Translate into deal language
This is where many diligence efforts fail. Investors don’t need more engineering detail; they need clarity: cost ranges, timing, severity, likelihood, detectability, and the practical path to mitigation.
6) Produce board-ready outputs
One-page summary, quantified risk register, and a capex/opex view that ties to the thesis. Appendices can be deep, but the front must be decisive.
The scope map: Data centers vs energy assets (and where diligence overlaps)
The most valuable diligence doesn’t treat data centers and energy assets as separate worlds. Investors increasingly buy systems—or assets whose performance depends on external systems (grid, utilities, networks, water, fuel logistics, regulatory constraints).
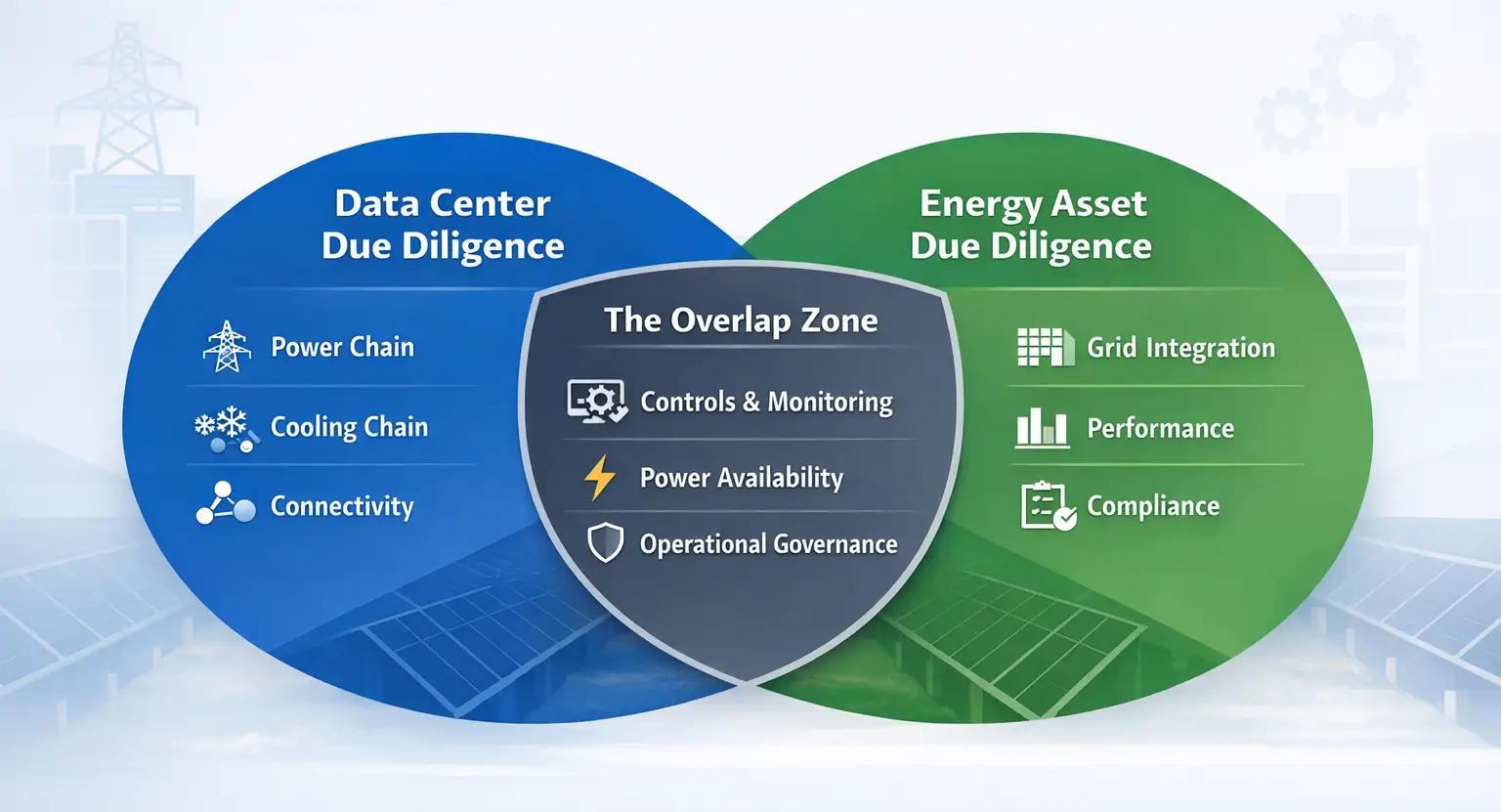
Data centers: the systems investors now underwrite
In mission-critical facilities, outages are rarely caused by a single “big failure.” They come from the gaps between design, operation, maintenance, and change.
Here are the six systems diligence must cover in an investor-grade way:
- Site constraints + expansion runway
- Power chain (utility → MV/LV → UPS → generation → distribution)
- Cooling chain (production → distribution → controls → heat rejection)
- Water and environmental dependencies
- Network connectivity + physical pathways
- Security + monitoring + operational governance
Energy assets: what investors verify before underwriting cashflow
Energy asset diligence often looks “engineering heavy,” but investors still want the same truth: performance under constraints and the reality of integration.
The diligence focus typically includes:
- Technology and performance realities (efficiency, degradation, operating envelope)
- Grid integration risk (connection capacity, curtailment exposure, compliance conditions)
- Controls and monitoring maturity (visibility, alarm integrity, response processes)
- Operational model (maintenance strategy, spares, vendor dependency, staffing)
- Regulatory readiness (what is permitted vs what is assumed)
Even when the asset is technically sound, investors care about the practical limiters: connection agreements, operational discipline, and what happens when the wider system is stressed.
Where it overlaps (and why investors care)
The overlap zone is where mission-critical deals get messy—and where diligence creates real value:
- Power availability and expansion drives both data center growth and energy integration assumptions.
- Controls, monitoring, and remote access are now top-tier risk factors across both domains.
- Operational governance (change control, testing culture, incident response) often predicts future reliability better than a design drawing.
This overlap is also where post-close integration can break resilience if it’s not planned.
Power availability risk: proving capacity, redundancy, and runway
Power is no longer just a technical topic—it’s a growth constraint, a contractual risk, and often the primary underwriting question.
Modern power diligence should answer:
- What is the proven available capacity, not the promised capacity?
- Where are the single points of failure under maintenance conditions?
- Is testing real, recent, and complete—or is it assumed?
- Can the facility scale without redesigning the electrical backbone?
Good diligence asks for evidence that power resilience exists in operations, not only on paper. This includes commissioning documentation, generator testing regimes, UPS maintenance records, breaker coordination logic, and observed operational behaviour during test windows.
Cooling and heat rejection: finding hidden constraints early
Cooling failures are often described as “capacity problems,” but in practice they’re commonly controls, maintainability, or operating envelope problems. A system can have enough nameplate capacity and still be fragile.
Investor-grade cooling diligence focuses on:
- The true operating envelope and seasonal constraints
- Maintainability (what happens when you take a unit out of service?)
- Controls stability (hunting, alarms, sensor integrity, response logic)
- Heat rejection dependencies and realistic failure impacts
- Operating history and any repeated nuisance alarms or excursions
Cooling diligence also needs to connect to expansion plans. Scaling can expose control weaknesses and distribution bottlenecks that never appear at lower loads.
Water risk: supply, permits, and operational exposure
Water used to be treated as a background utility. In 2026, it’s often a constraint—and sometimes a deal risk.
Investor-grade water diligence asks:
- What are the dependencies (municipal supply, on-site storage, treatment)?
- What is the permit reality vs the assumption?
- What happens during restrictions or supply disruptions?
- Are there hidden operational costs in treatment, discharge, or compliance?
This matters because water limitations can turn into uptime limitations, and compliance issues can become capex shocks. Water risk also affects scalability. A site might be viable today but constrained under expansion.
Security: physical + cyber, and the “who can touch what” question
Security diligence has matured fast because threat models and operational realities changed. For investors, security risk isn’t only about a breach headline. It’s also about operational safety, change control, and the integrity of monitoring and remote access.
Investor-grade security diligence should cover physical security, cybersecurity, and governance—especially where OT systems are involved.
A few security diligence questions investors now ask more directly:
- Who has remote access to critical systems (vendors included)?
- Are OT networks segmented in practice, not just in diagrams?
- Are access logs and alerts reviewed, or simply stored?
- Is there a clear ownership model for controls systems, monitoring, and response?
Security becomes particularly fragile post-close, when access control and vendor relationships change.
Scalability without surprises: the constraint chain test
Scalability is frequently oversold. Investors hear “we can expand” and assume it’s a straight line. In reality, expansion is a chain of constraints—each one must hold, or the plan breaks.
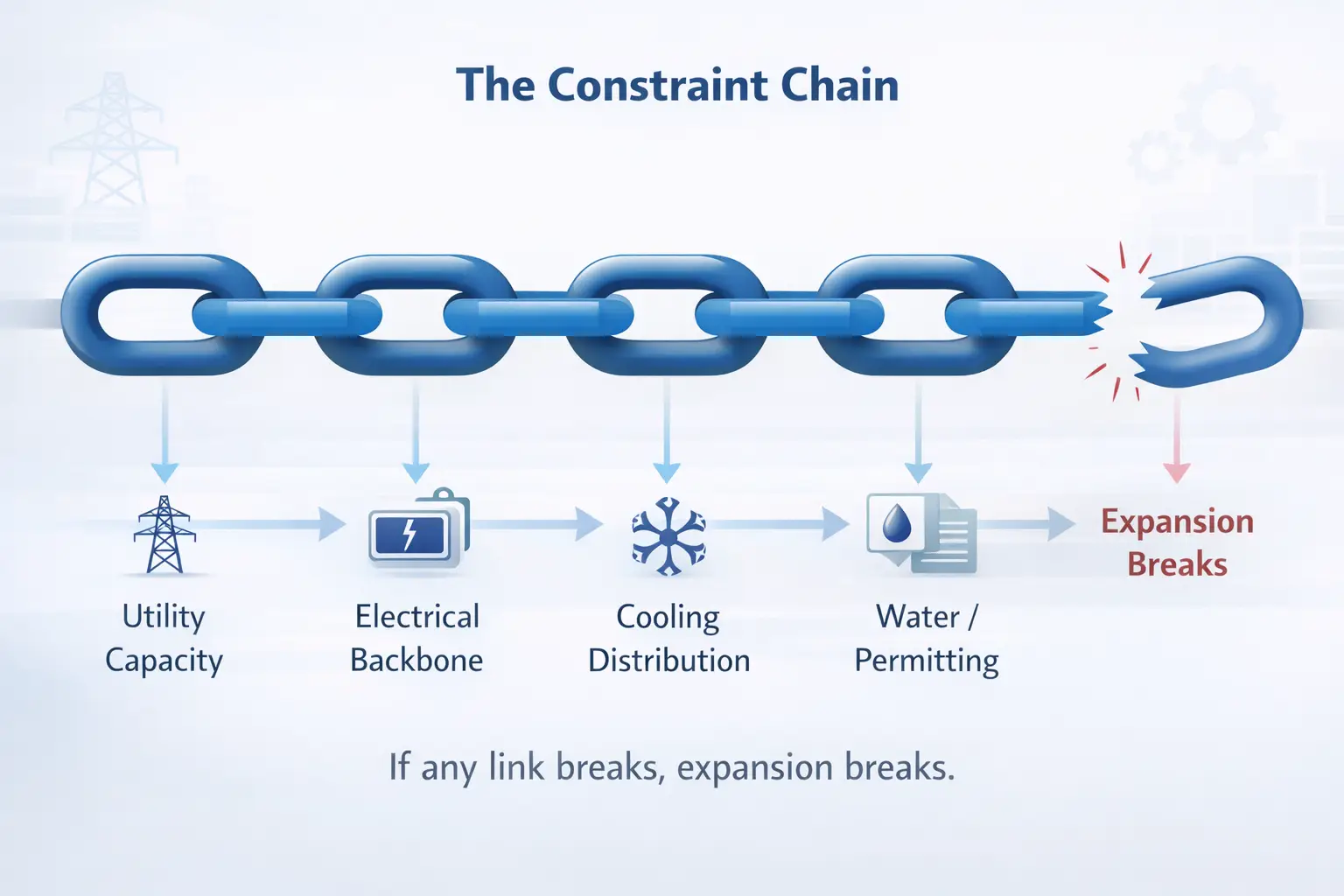
Investor-grade scalability diligence verifies:
- Electrical backbone capacity and upgrade path
- Cooling distribution scalability, not only plant capacity
- Space and maintainability constraints (layout realities matter)
- Permitting and compliance conditions for expansion
- Delivery feasibility (lead times, outages during tie-ins, sequencing)
A site can be resilient today yet fragile during expansion. That transition risk should be explicitly assessed and quantified.
Quantifying resilience: moving beyond tiers and marketing
Resilience is now a pricing variable. But most organisations still describe resilience using labels instead of evidence.
Investor-grade resilience is built from three layers:
- Design resilience – What the architecture intends (redundancy, diversity, separation).
- Operational resilience – What the organisation actually does (testing culture, maintenance maturity, procedures, spares strategy, response capability).
- Supply resilience – What the asset depends on (utility stability, fuel logistics, water availability, vendor support, parts lead times).
When investors ask for “resilience,” they increasingly want a scorecard they can apply across assets, not a narrative description.
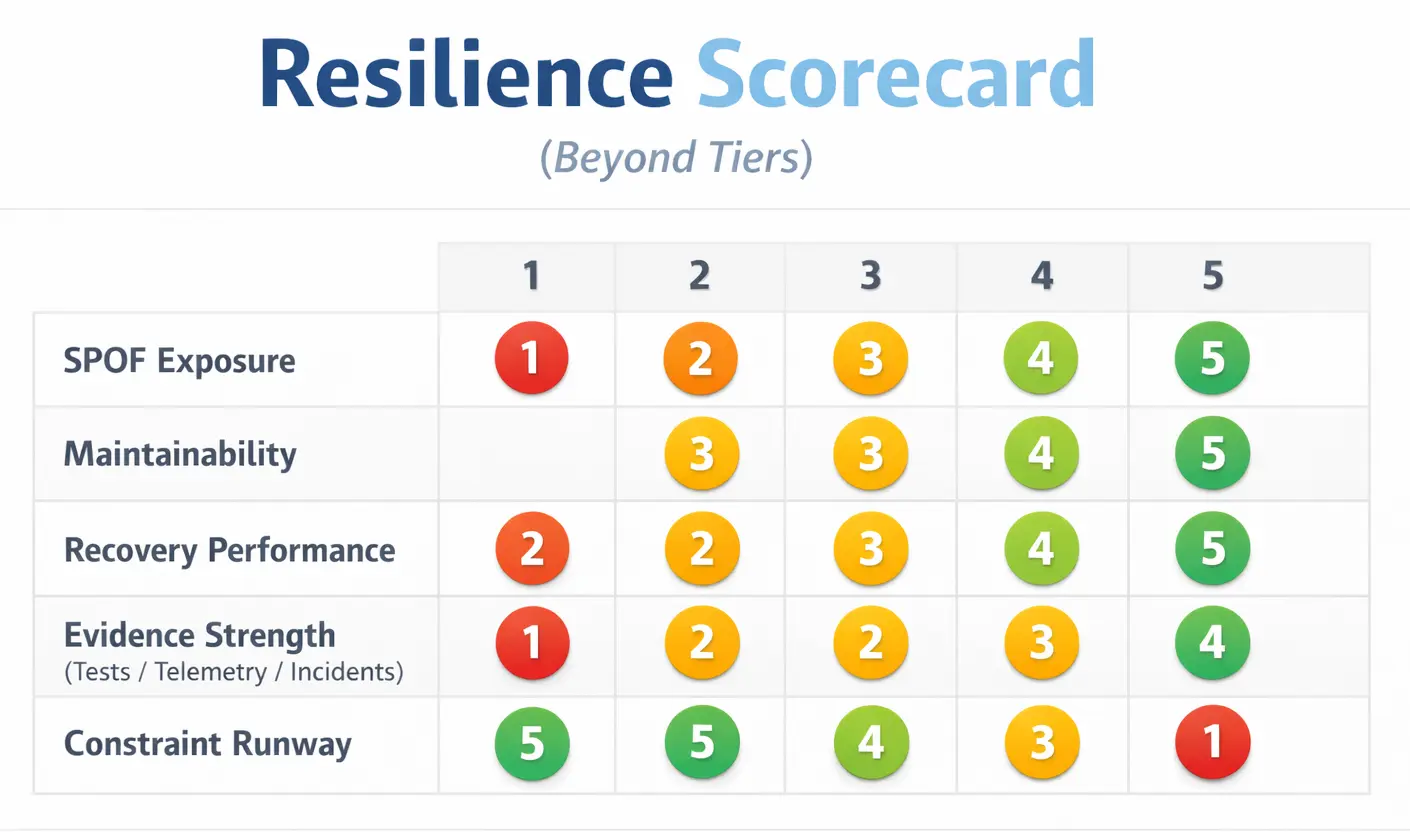
A practical resilience scorecard can include:
- SPOF exposure (including during maintenance and failure cascades)
- Maintainability (can you service without taking disproportionate risk?)
- Recovery performance (time-to-recover, not just redundancy count)
- Evidence strength (tests, telemetry, incident history)
- Constraint runway (how close is the asset to hard limits?)
From findings to numbers: capex, opex, and constraint-based valuation
This is where TDD becomes truly investor-grade. Every technical finding should land in one of three buckets:
1) Deal breakers
Issues that undermine the investment thesis: no viable power runway, unmanageable compliance exposure, structural constraints that block growth, critical safety risk, or unacceptable operational fragility.
2) Price and terms issues
Findings that drive re-trade, escrow, warranties, or covenant tightening. These often include latent defects, non-compliant configurations, missing test evidence, or capex that must occur before the asset can deliver expected revenue.
3) Value creation opportunities
Upgrades that improve margin or reduce risk: efficiency gains, controls improvements, monitoring maturity uplift, and staged expansion plans that make growth more reliable.
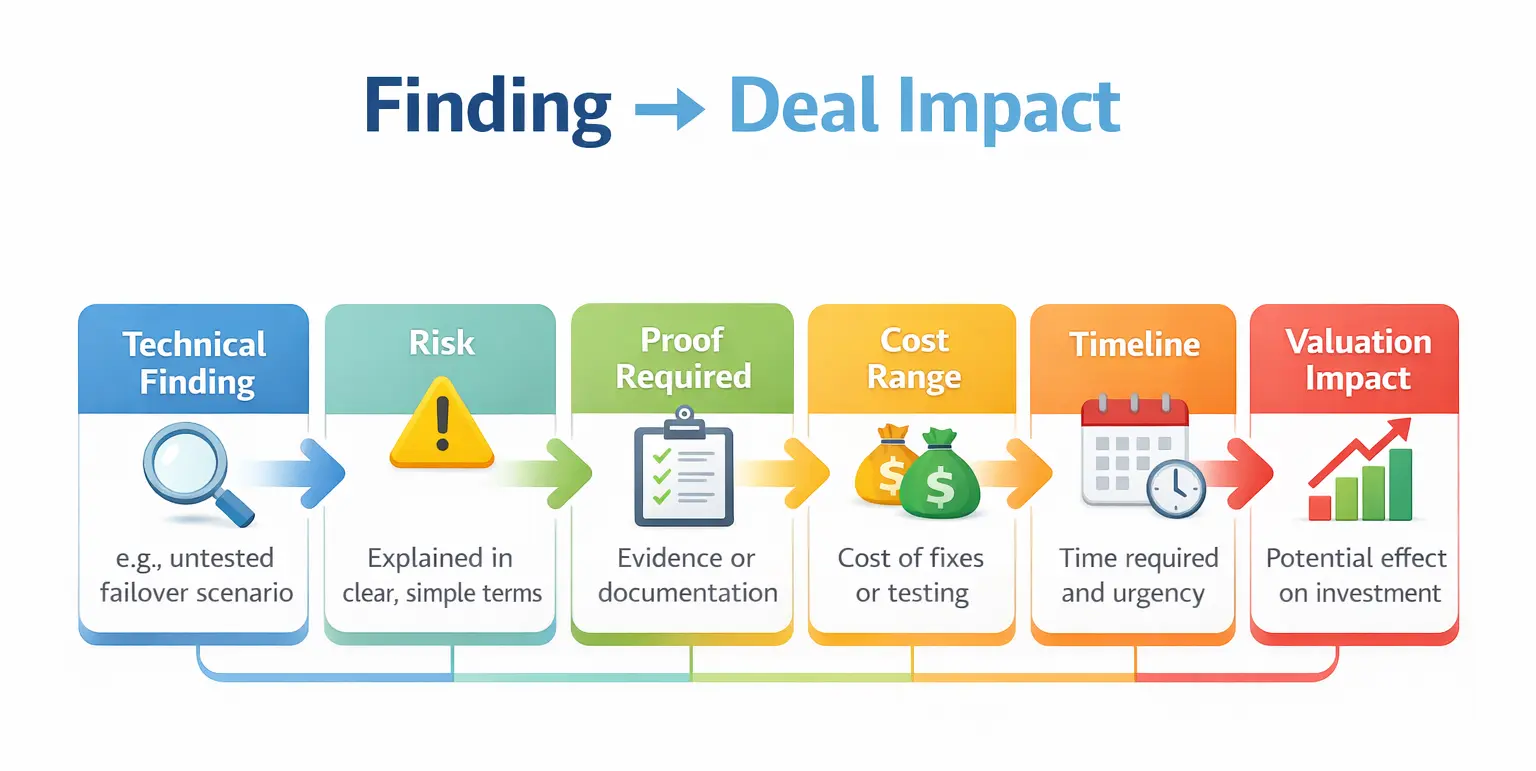
A simple way to present this for investment committees is a “translation line” per finding:
- Finding → Evidence → Risk level → Cost range → Timeline → Business impact
That keeps the report decisively commercial without losing technical credibility.
M&A integration risks: network, OT/IT boundaries, and monitoring
A large percentage of “technical risk” emerges after close. Not because the facility suddenly changes, but because the operating model and system ownership changes. Integration introduces new failure modes.
Three integration risk categories repeatedly show up in mission-critical acquisitions:
- Monitoring integrity risk – Alarm routing, thresholds, escalation, and dashboards get “standardized” and visibility gets worse. This is where silent failures start.
- OT/IT boundary risk – Remote access paths, vendor VPNs, patching responsibility, identity management, and segmentation assumptions collide. The question becomes: who owns what, and how is it controlled?
- Network and connectivity risk – Carrier diversity isn’t just “two providers.” It’s physical route diversity, pathway separation, contract realities, and the operational plan for changes.
Red flags that trigger re-trade (and the proof needed to defuse them)
Investors don’t re-trade because of “technical complexity.” They re-trade because the diligence evidence suggests the risk is larger—or sooner—than expected.
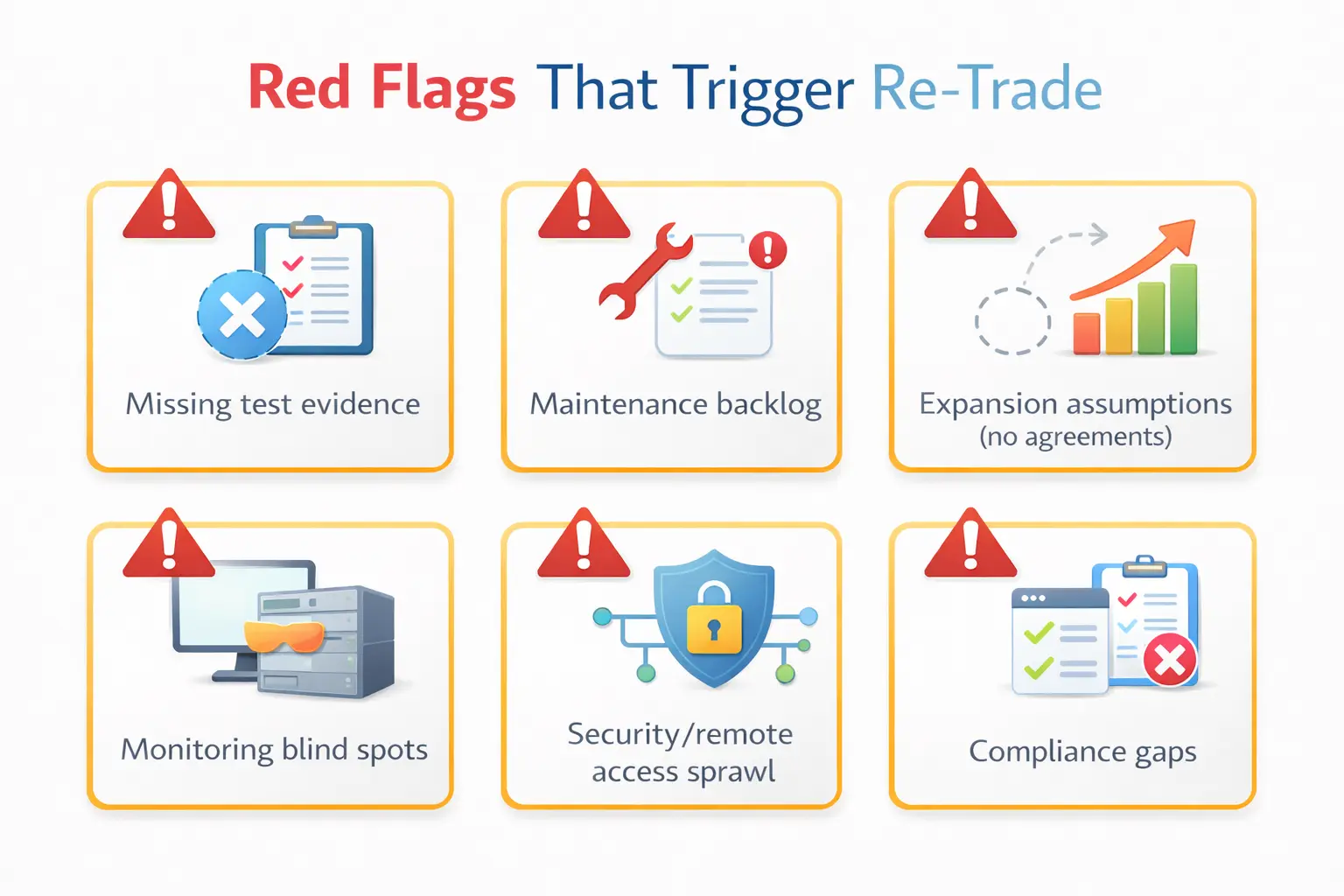
Common triggers include:
- Missing or weak testing records for critical power and safety systems
- Maintenance backlog that implies hidden capex or operational fragility
- Expansion plans that depend on assumptions, not agreements or proven capacity
- Monitoring and controls gaps that reduce detectability and response reliability
- Security and remote access arrangements that can’t be cleanly governed post-close
Most of these can be mitigated. But mitigation requires evidence and a practical plan—not reassurance.
Board-ready deliverables: what a bankable TDD report includes
A “bankable” diligence package is not defined by page count. It’s defined by clarity, evidence, and commercial translation.

At minimum, investor-grade outputs should include:
- Executive summary (one page): top risks, top opportunities, thesis alignment
- Quantified risk register: severity, likelihood, detectability, mitigation path
- Capex/opex view: “must-do” vs “planned” vs “optional” with timing
- Resilience scorecard: evidence-based and comparable across assets
- Integration memo: monitoring, OT/IT, network, and post-close priorities
- Appendices: drawings reviewed, evidence list, assumptions and limitations
Final takeaway: diligence is now about survivability and runway
In 2026, technical due diligence is no longer a static review of design intent. It’s an evidence-led assessment of survivability, constraint runway, and integration readiness.
Investors don’t need more technical jargon. They need confidence that the asset can deliver the thesis under real operational conditions, and a clear plan for what must change to reduce risk or unlock value.
Investor-grade TDD for mission-critical assets
If you’re acquiring, refinancing, or scaling a mission-critical asset, the goal is simple: reduce surprises and protect the thesis.
We support investors and operators with diligence that is evidence-led, board-ready, and built around real-world operational survivability—across data centers and energy-linked infrastructure.
Turn Technical Risk Into Investment-Grade Confidence
Azura Consultancy — Technical Due Diligence Services (Investor-Grade)
Azura Consultancy provides Technical Due Diligence (TDD) for mission-critical and infrastructure assets, helping investors, lenders, and owners understand what’s really behind the drawings, claims, and operating metrics.
Our work combines site inspections, technical document reviews, data analysis, and stakeholder interviews to identify risks, verify performance, and surface practical upgrade paths.
If you’re planning a data center, district energy system, smart city platform, telecom network, or power project—these themes (power availability, water constraints, reporting KPIs, heat reuse, and delivery risk) should be treated as investment-grade diligence questions, not just design talking points.
Azura Consultancy’s Technical Due Diligence expertise helps you test survivability early: validating constraint runway (power/water/permitting), checking scalability and integration readiness across MEP + OT/IT monitoring and controls, and translating technical findings into timeline, capex/opex, and valuation impact—so decisions are made with evidence, not assumptions. Learn more on our Technical Due Diligence Services page:
We deliver TDD across a range of asset types—especially where availability, resilience, compliance, and expansion feasibility directly affect value. This includes:
- Data centers (power and cooling systems, resilience/redundancy, scalability, security, compliance)
- Power plants (design, equipment, construction, operational readiness, regulatory alignment)
- District energy / district cooling / district heating (generation + distribution performance, reliability, scalability, compliance)
- Renewable energy projects (site/resource assumptions, engineering/design, performance and reliability, risk/opportunity mapping)
Where the transaction requires it, we also support Lender’s Technical Advisory / Lender’s Due Diligence (LTA)—translating technical findings into decision-ready risk and mitigations for financing committees.